Presentation Templates
To use Paradym to verify information from a holder you’ll first need to create a presentation template. A presentation template defines what attributes and/or information the holder should present as proof. Once created, a template can be used to request as many presentations as you want.
Overview
When creating your presentation template you are basically making the blueprint for a presentation request that can be re-used. The main things you need to know before creating a template are:
- The credential format and type of the credential(s) you want to request
- The trusted issuer(s)
- The specific attributes you want to request
- [Optional] Any requirements the specific attributes need to match
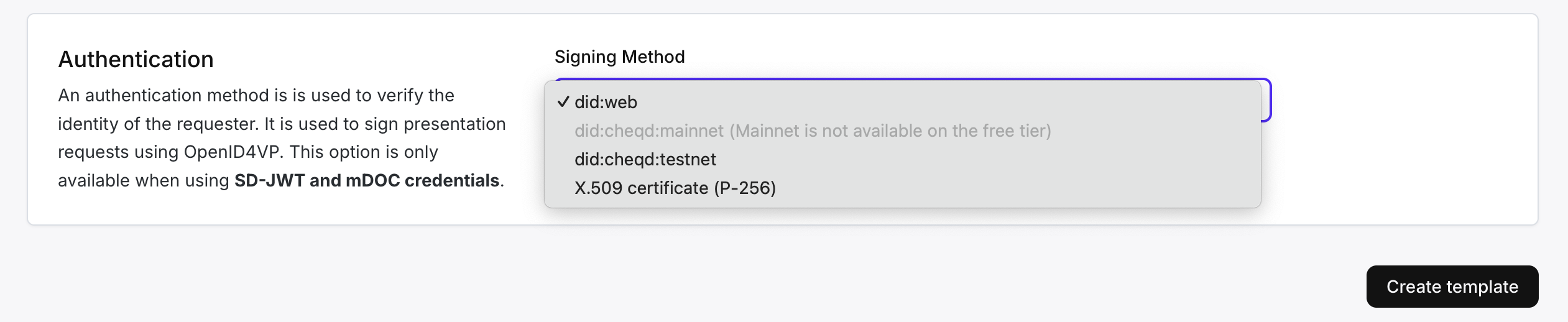
- [Optional] The request authentication method when using
sd-jwt-vcormdoccredentials
Note that it is currently not possible to combine all credential formats in a single presentation template. You have to decide which credential format to request, and this will also influence the exchange protocol to use for the request. Based on the format that is going to be used for issuance of the credential, you need to use the same format for verification of the credential:
sd-jwt-vcandmdocwith OpenID4VC Verification .anoncredswith DIDComm Verification .
We recommend to always configure the trusted issuers on a presentation template, as everyone can issue a credential based on a certain credential type. It is the issuer of the credential that determines whether you trust or accept it. If you don’t configure the issuers on a presentation template, you must manually verify the issuer of a submitted credential afterwards and ensure you trust the issuer of that credential. Read more on creating and configuring trusted entities.
If you’re verifying a credential issued by one or more issuer(s) that is not yourself, you need to get hold of the following information to be able to verify credentials issued by them:
- The credential format. Paradym supports
sd-jwt-vc,mdocoranoncredsfor verification. - The trusted issuers. Paradym supports X.509 certificates and DIDs.
- The attributes of the credential.
Presentation Template Contents
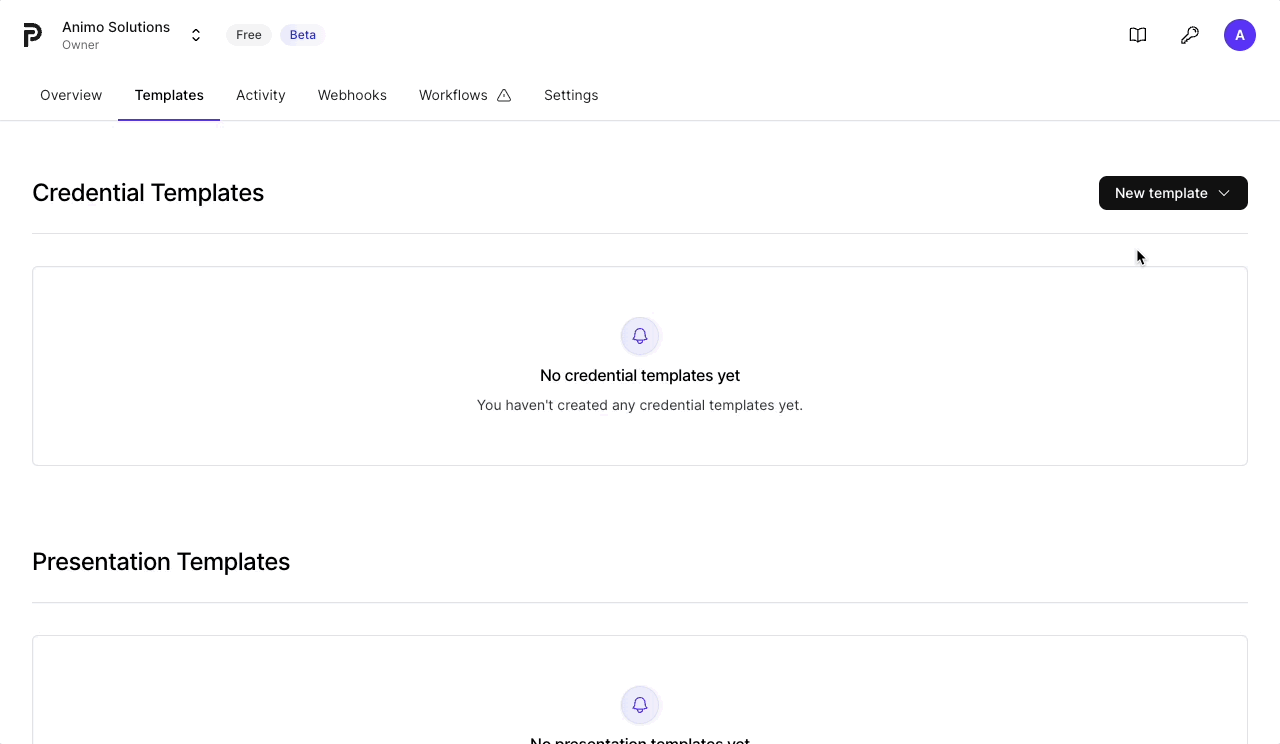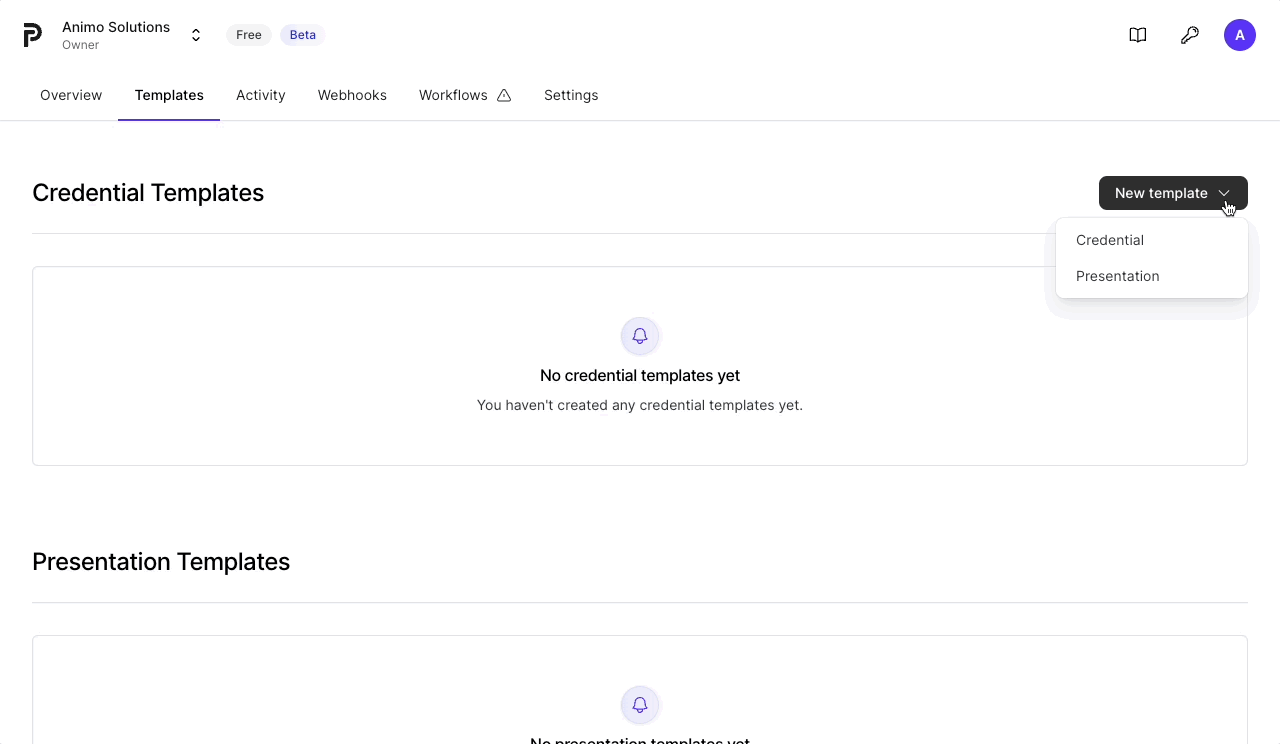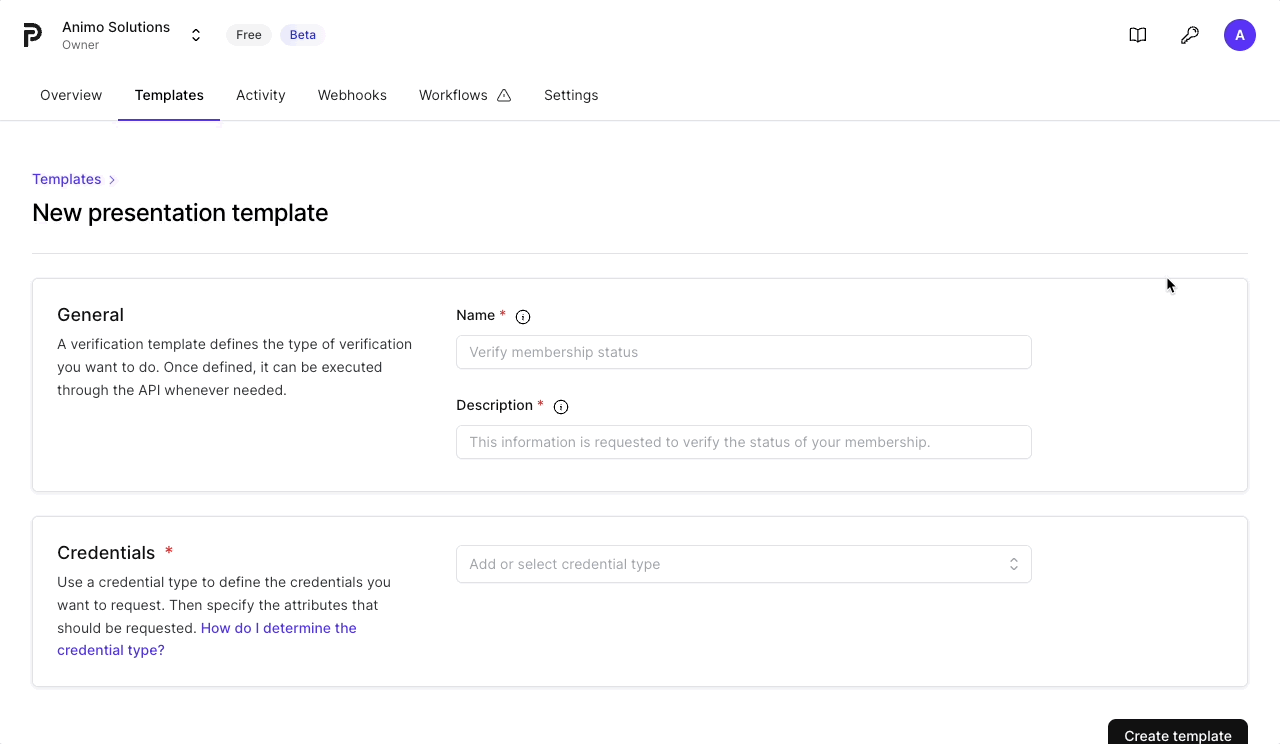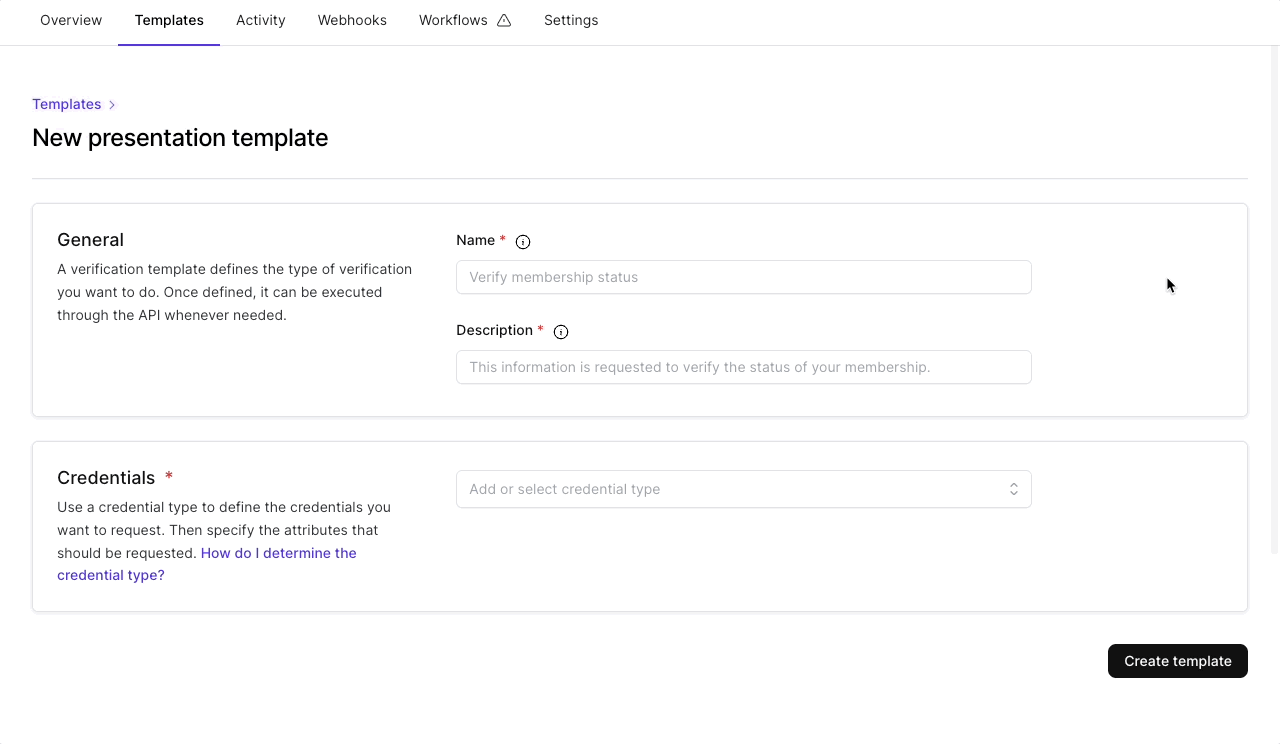
Each presentation template contains some general information like a name and description, which will be visible to the recipient of the verification request. The description is specifically important as it will show the recipient why the information is requested.
Credentials
In addition to the general information, each presentation template needs to define one or multiple (up to 20) credentials that will be requested.
This is where you add a credential type as well as the specific fields you want to request. The type (SD-JWT VC and mDoc) or schema (Anoncreds) of the credential is a unique and re-usable identifier that can be used to request a presentation involving this specific credential type. For example a verifier might specify that they want to verify attributes as defined in a mobile drivers license (mDL) and use the org.iso.18013.5.1.mDL doctype (as specified in ISO 18013-5). The credential type can be selected from previously created paradym credential types, or it can be added manually for other types.
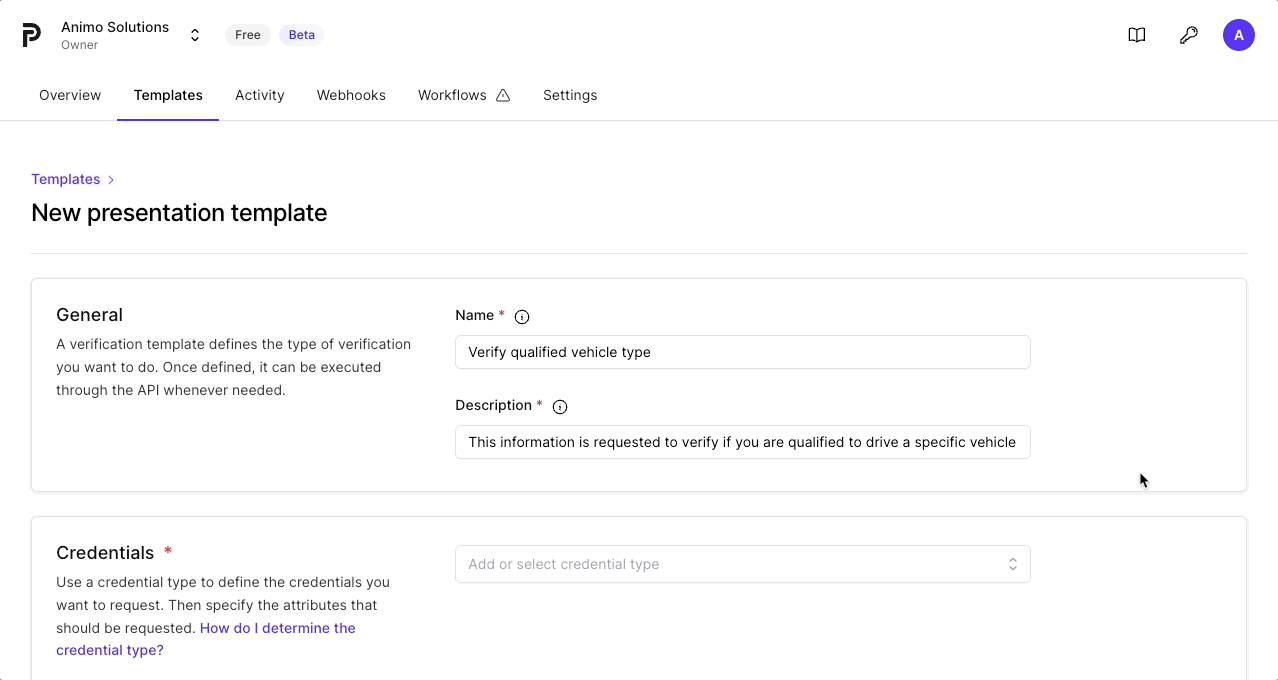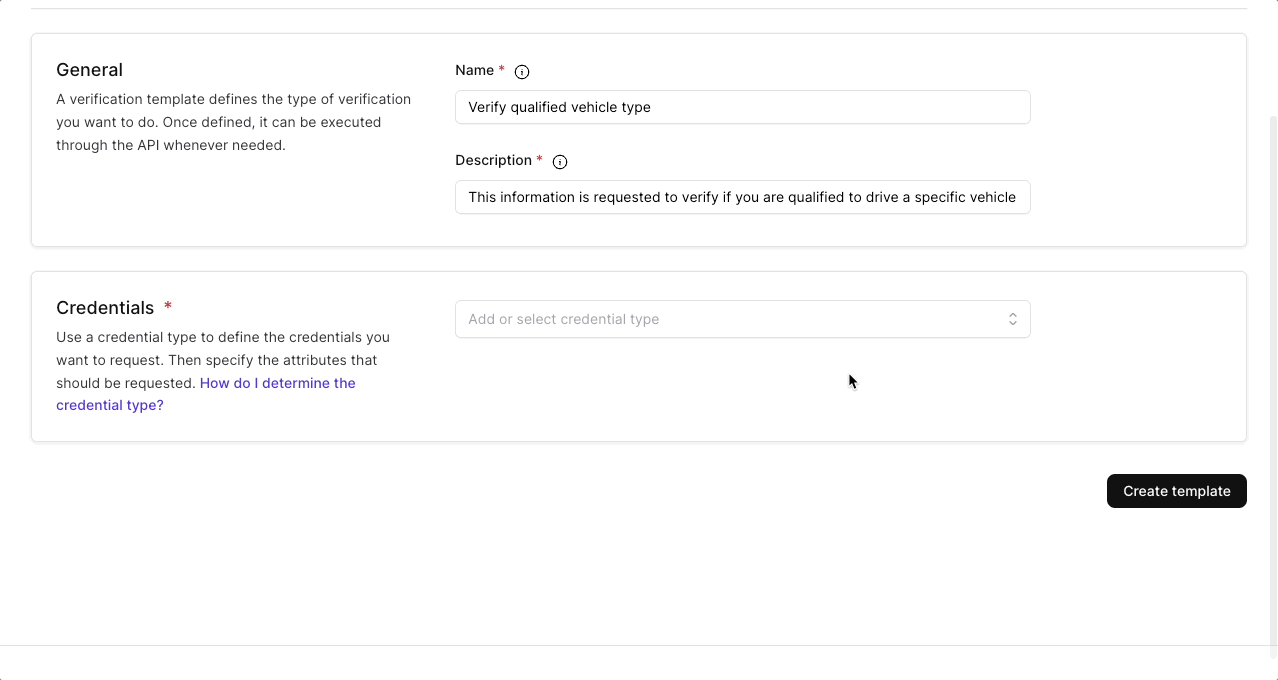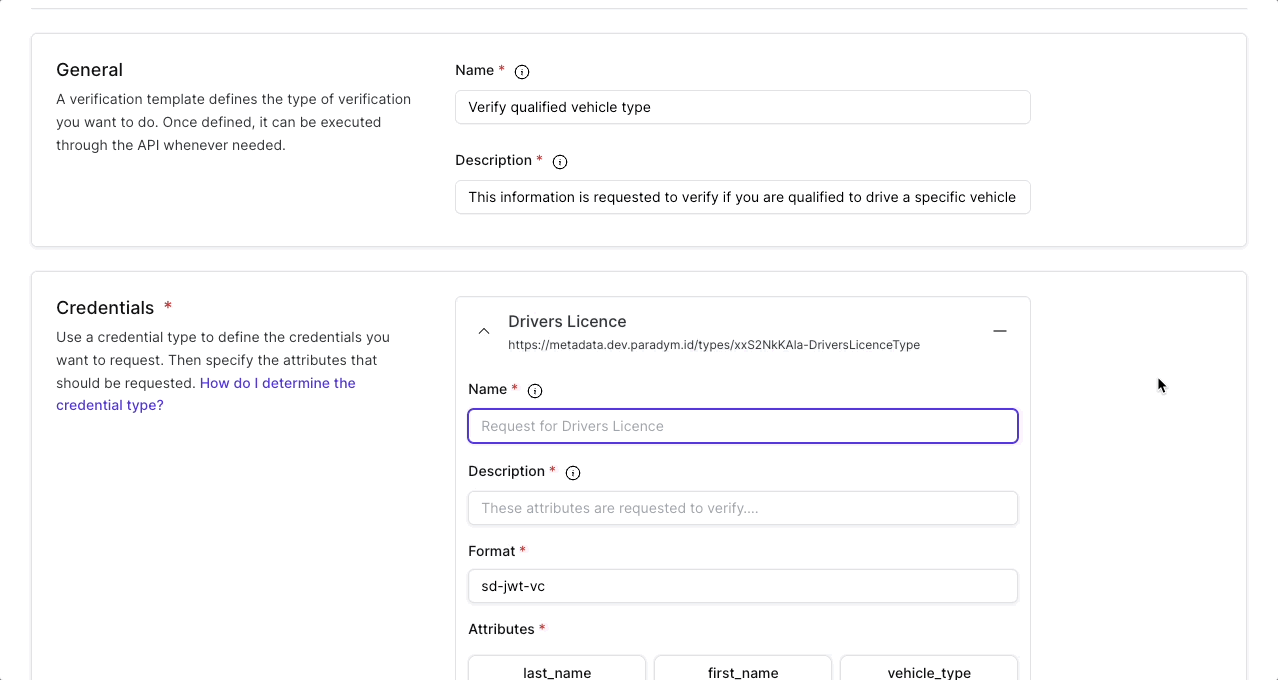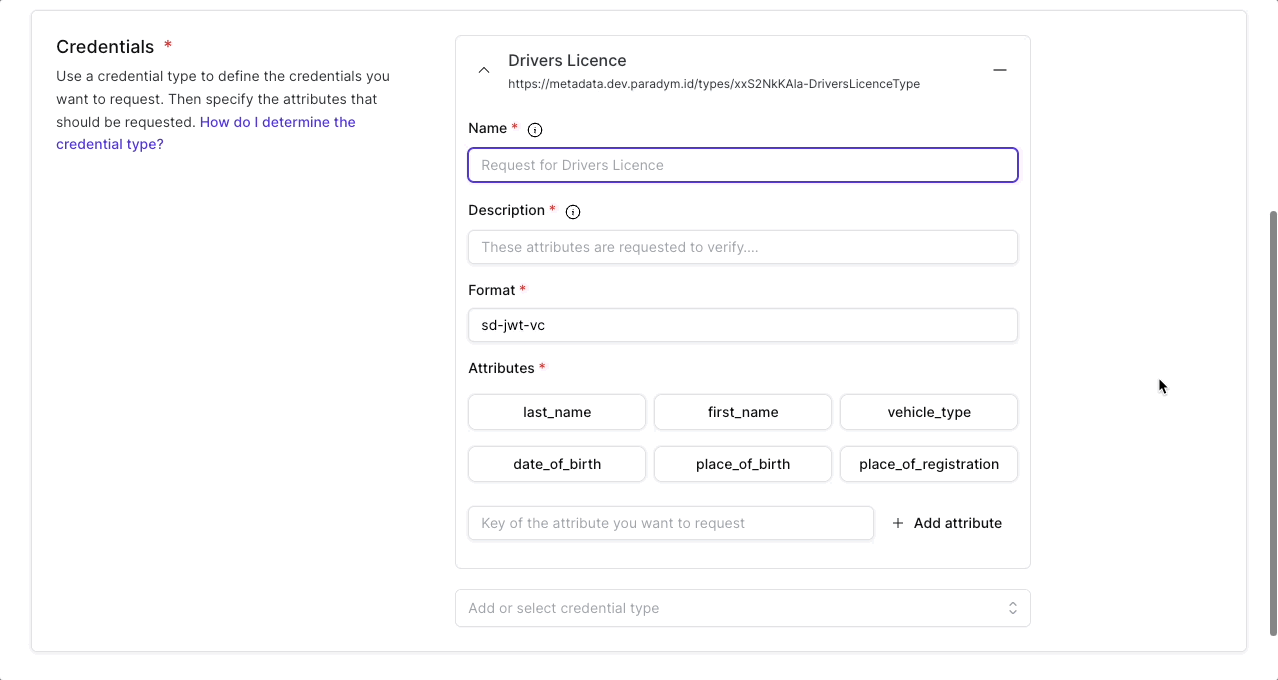
For each credential you want to include in the presentation request a name and description can optionally be provided. Currently the individual credential names and descriptions are not shown to the recipient, but are used in the dashboard to provide additional context.
- The format of the credential is where you define what kind of verifiable credential you will request from the wallet. Each format has its own benefits and features. Currently Paradym supports SD JWT VCs (
sd-jwt-vc), mDoc (mdoc) and Anoncreds (anoncreds) for presentation templates. Read more about the different standards and protocols.
The attributes are where it gets specific.
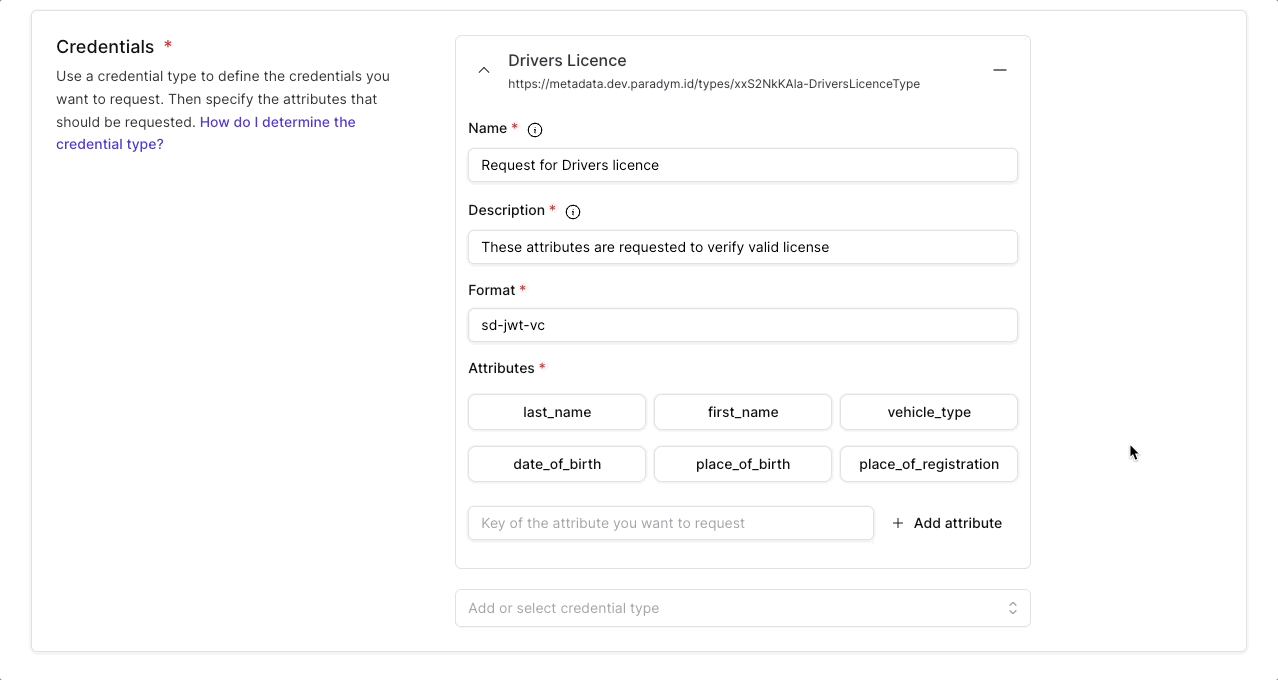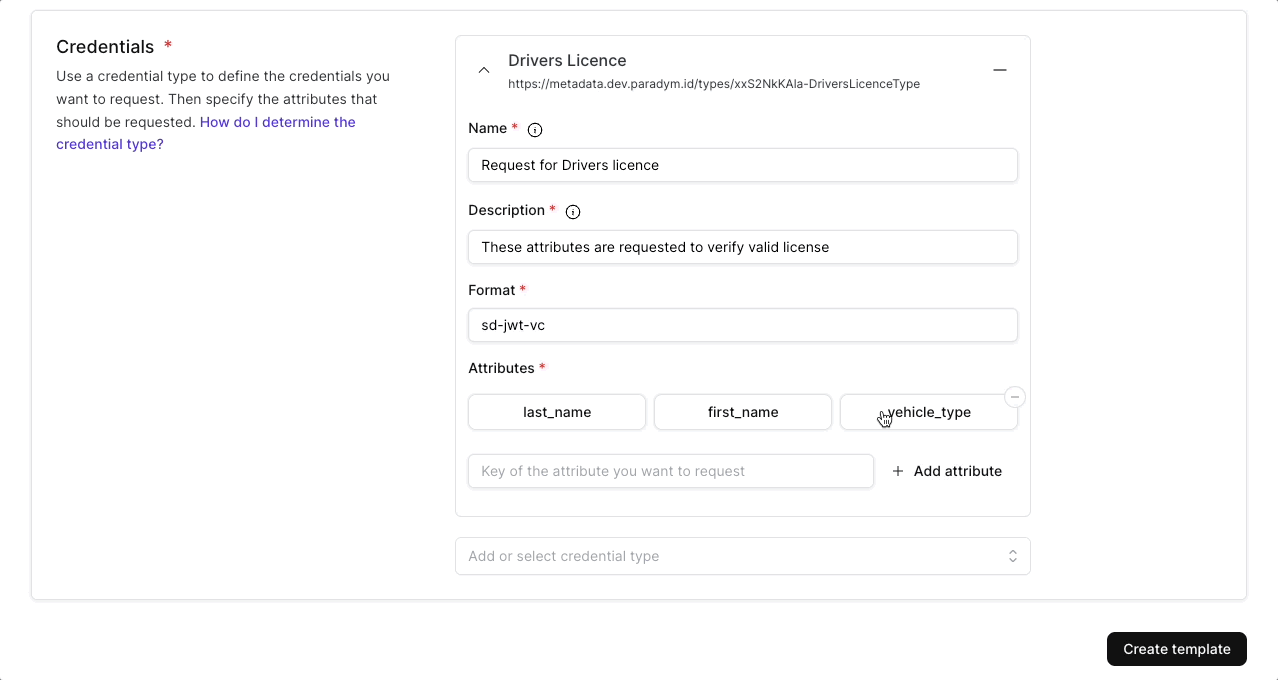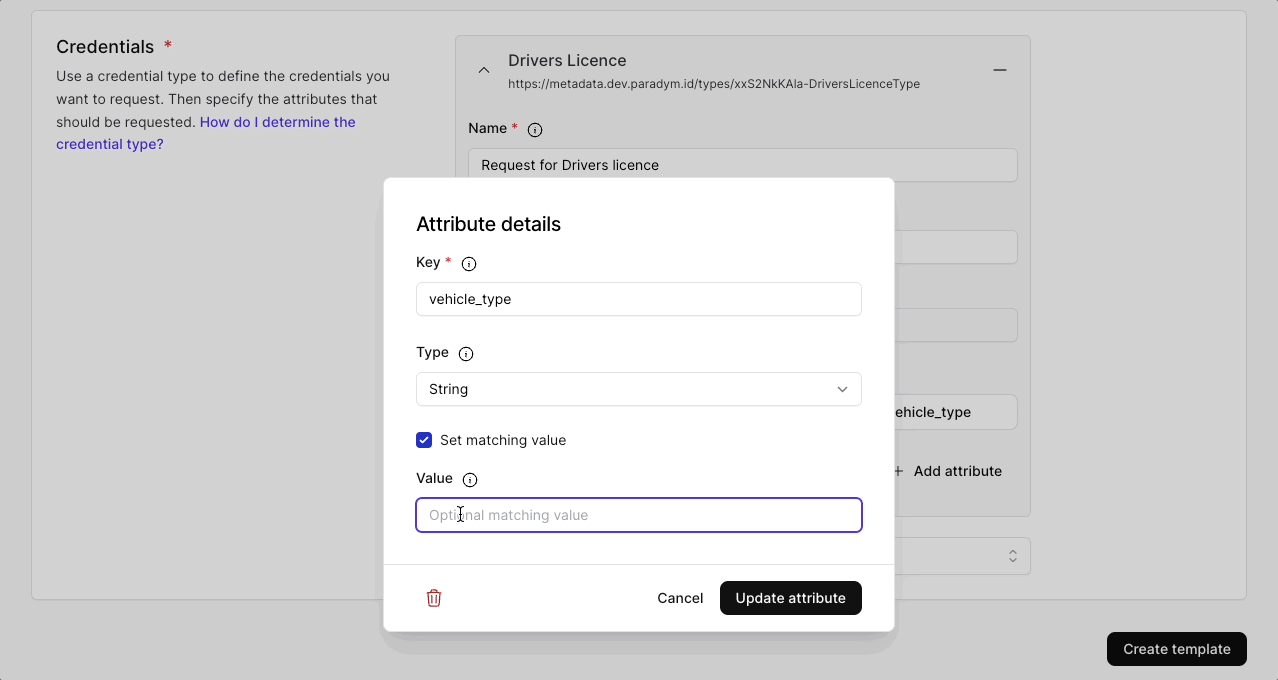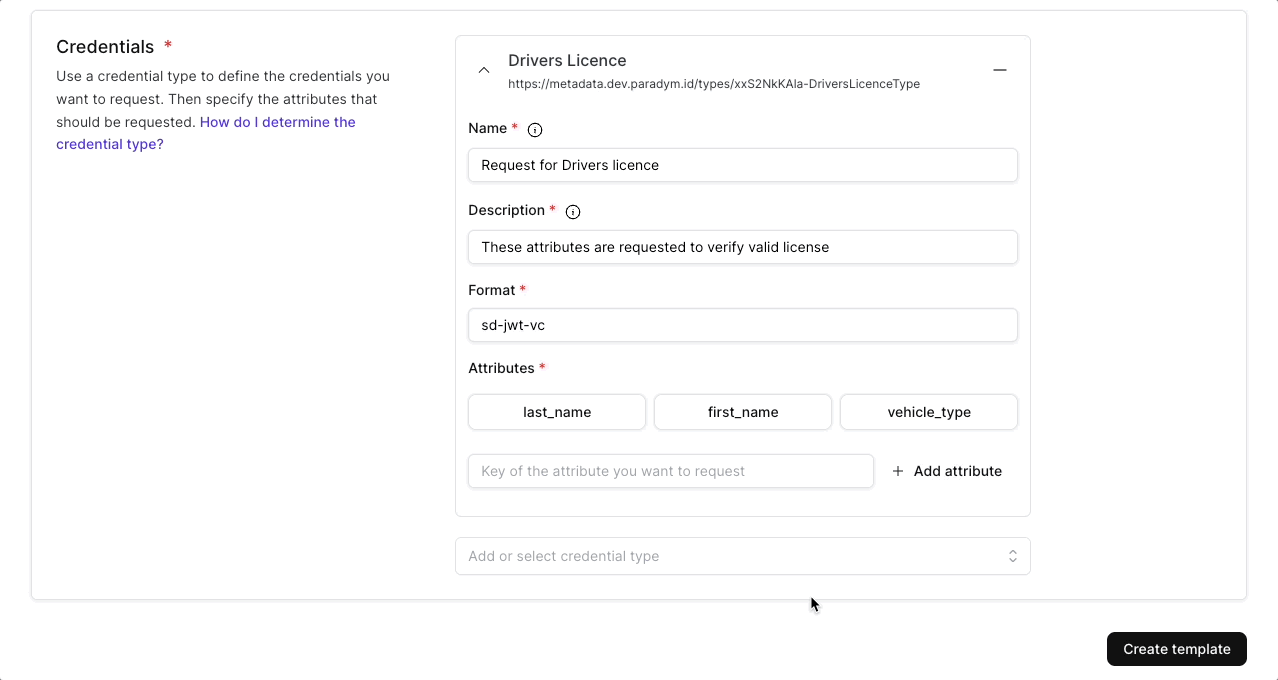
- With the attribute key, information from the attribute can be requested in a proof request programmatically (e.g. request the value of job-title). If only the key is defined then the proof request (if accepted) will return the value of this key from this credential type.
- Additionally you can optionally define the attribute type, with which the request can be further specified (e.g. request the value of job-title only if it is a string type). The available types are
string,number,boolean,date, andobject. - As a third level, you can define the specific value (e.g. request the value of job-title only if it is a string type AND only if it matches
developer) - For number values you can also define a range (minimum, maximum, or both). Anoncreds credentials support range proofs, and only whether the value lies within the range will be shared (true or false), not the actual value. This allows you to verify someones date of birth is before 20001012 (12 october 2000), without actually getting to know their date of birth.
Not all credential formats support all types. SD-JWT VC supports all types, and Anoncreds supports only date and number.
mDoc supports all types as values in an issued credential, but does not allow specifying the type or value of an attribute in a presentation template. This limitation is defined in ISO 18013-7 and enforced by Paradym to maximize interoperability.
Creating a presentation template
Creating your first presentation template is easiest to do within the dashboard, especially if you want to create a presentation request using a credential template you’ve created. It guides you through configuring the elements of the presentation request.
If you’re going to use the API to create a presentation template, and you’ve created a presentation template before from within the dashboard you can retrieve it from the API (Retrieve Presentation Template ) and use that for creating a similar presentation template using the API.
The easiest way to get started with the API is using the interactive API Reference . If you would like to follow along using a custom API client, make sure follow the Quickstart guide. You can read more on interacting with the API.
To create a presentation template in the API we will make a POST request to https://api.paradym.id/v1/projects/{projectId}/templates/presentations. For detailed information on the endpoint, refer to the create presentation template page in the API reference.
When creating a presentation template through the API you can optionally also provide a list of trusted issuers and an authentication method. Read the docs on trusted entities to learn more about creating and linking a trusted entity to a presentation template.
SD JWT VC
For credentials with sd-jwt-vc format, we need to provide a type value. You can copy this from your credential template, or someone else can share this with you. Make sure to change the attributes based on your credential template.
{
"name": "Verify membership status",
"description": "This information is requested to verify if you are still and active member",
"verifier": {
"signer": "certificate",
"keyType": "P-256"
},
"credentials": [
{
"description": "These attributes are requested to verify your paradym membership",
"name": "Request for Paradym MemberCard",
"format": "sd-jwt-vc",
"type": "https://metadata.paradym.id/types/28dc88-MemberCard",
"trustedIssuers": ["cm85v8gnx003wuqnk31p2k80x"],
"attributes": {
"first_name": {
"type": "string",
"value": "myValue"
},
"loyalty_points": {
"type": "number"
},
"active": {
"type": "boolean",
"value": true
}
}
}
]
}mDoc
Requesting an mDoc credential in a presentation template is similar to an SD-JWT VC, and can even be combined in one request with SD-JWT VC credentials. Some differences:
- mDoc credentials do not support specifying the types or values of attributes, neither is requesting nested attributes possible. Only the top-level attributes you want to request from which namespaces can be configured.
- mDoc credentials are structured based on namespaces. An mDoc can contain multiple namespaces, and each namespace can contain attributes. An example is the
org.iso.18013.5.1namespace, which contains thegiven_nameattribute. - mDoc credentials support an additional
intentToRetainproperty, which is defined in ISO 18013-5 and defines whether the value will be retained (stored) after the verification is processed. The default value isfalse, but should be changed if you will store the value. Changing this value does not affect processing in Paradym, and merely acts as a hint to the wallet.
{
"name": "Rent a car",
"description": "To rent a car we need to verify your drivers license",
"verifier": {
"signer": "did:web"
},
"credentials": [
{
"format": "mdoc",
"type": "org.iso.18013.5.1.mDL",
"trustedIssuers": ["cm85v8gnx003wuqnk31p2k80x"],
"attributes": {
"org.iso.18013.5.1": {
"properties": {
"family_name": {},
"given_name": {
"intentToRetain": true
},
"driving_privileges": {
"intentToRetain": false
}
}
}
}
}
]
}Anoncreds
Requesting an Anoncreds credential in a presentation template is very similar to an SD-JWT VC, however there are some differences:
- Anoncreds credentials only support
stringandnumbertypes. Forbooleantypes you can usenumberwith values1and0. Fordatetypes you can usenumberand encode the date asyyyymmdd. This allows you to do range predicate checks, e.g. requesting thatdate_of_birthis less than20001012(before 12 october 2000). - You need to provide a
schemainstead of atypeto indicate which credential type should be requested.
{
"name": "Verify membership status",
"description": "This information is requested to verify if you are still and active member",
"credentials": [
{
"description": "These attributes are requested to verify your paradym membership",
"name": "Request for Paradym MemberCard",
"format": "anoncreds",
"schema": "did:cheqd:testnet:fb8a3467-a72d-41d7-bde0-50c85febbef4/resources/efd5749c-fff5-4dfc-9e30-d75ec92f15da",
"trustedIssuers": ["cm85v8gnx003wuqnk31p2k80x"],
"attributes": {
"first_name": {
"type": "string"
},
"loyalty_points": {
"type": "number",
"minimum": 500
},
"active": {
"type": "number",
"value": 1
}
}
}
]
}The return value will be approximately the same as the payload you provided, with a few extra fields (such as id, createdAt, and updatedAt) added.
Even though the examples above are all separate per format, it is possible to mix sd-jwt-vc and mdoc credentials in one presentation template.